Microsoft Word app icon

XLoader is a malware tool that has been around for years, and now it is creeping out of the dark yet again with a focus on work environments.
XLoader is one of the more common tools that attackers utilize to try and gain information from infected systems. When XLoader appeared on macOS in 2021, it was billed as the fourth most-used tool that year.
Unlike in 2021, this latest XLoader variant is not intended strictly for the Java Runtime Environment, which means it has the potential to be much more dangerous. This latest form is written in the C and Objective C programming languages, and as noted by SentinelOne, signed with an Apple developer signature.
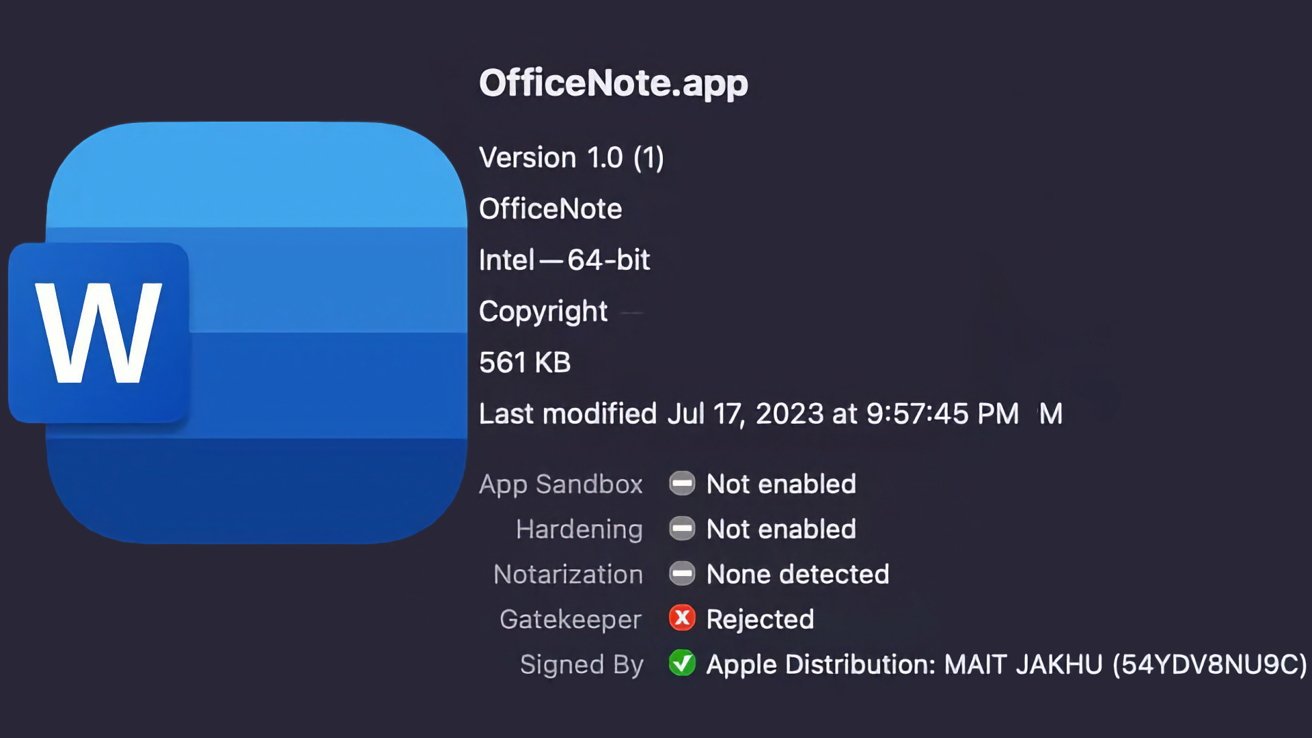
XLoader's latest cover is a Microsoft-branded Office productivity app called "OfficeNote." It's being distributed within a standard Apple disk image named "OfficeNote.dmg," which is automatically something you should be on the lookout for, especially in a work environment.
The developer signature is "MAIT JAKHU (54YDV8NU9C)," another key detail to be aware of.
According to the original report, Apple has already revoked that particular developer signature. However, SentinelOne says, "Apple's malware blocking tool, XProtect, does not have a signature to prevent execution of this malware" at the time of publication.
This particular malware tool has apparently been widely distributed as of July of 2023, when it first cropped up.
And macOS malware tools run a premium, based on advertisements found on crimeware forums. Renting this XLoader variant is going for $199 per month, or $299 for three months.
Compare that to the $59 per month, or $129 for three months the Windows-based version typically rents for.
If a person does install the XLoader malware tool onto their system, it will immediately target two popular browsers: Chrome and Firefox. It will then try and steal information that's stored in the user's clipboard via Apple's own API.
Apple's Safari is not targeted with this variant of XLoader.
Once installed, the malware tool will automatically deposit its payload into the user's home directory and execute. It will then create a hidden directory and a barebones app, while a LaunchAgent is then dropped into the user's Library.
This variant of XLoader is specifically designed for work environments, and it is advised IT security teams install third-party services designed to identify malware to prevent installations.
How to stay safe
As mentioned above, utilizing a software security service that can identify malware tools such as this one are important, especially for businesses. And of course, another easy way to stay safe and avoid malware tools is to avoid downloading any software or apps that you do not recognize.
macOS is still the safer option when it comes to malware tools like this, but the threats are growing. There are even attacks out there designed for Apple Silicon. Stay vigilant, even if you are on a Mac.