Apple is taking steps to increase security for people like journalists, activists, and politicians with a new setting in iOS 16, iPadOS 16, and macOS Ventura called Lockdown Mode. This setting hardens an iPhone, iPad, or Mac’s defenses in ways that interrupt methods we’ve seen used to compromise devices for highly targeted attacks.
Lockdown Mode blocks many message attachment types, disables link previews, turns off certain web browsing technology by default, blocks invitations and FaceTime calls from unknown sources, locks down wired connections to computers or accessories while the device is locked, and disables the ability to add new configuration profiles or enroll in mobile device management (MDM).
These are the areas that we know can be vulnerable, as Google’s Project Zero team detailed how iPhones of people targeted by the Pegasus software could be compromised in a “zero-click” scenario by using a GIF to exploit iMessage in the background. Other attacks have repeatedly targeted MDM solutions or used malicious websites to exploit flaws in rendering, and Lockdown Mode closes those doors from the start.
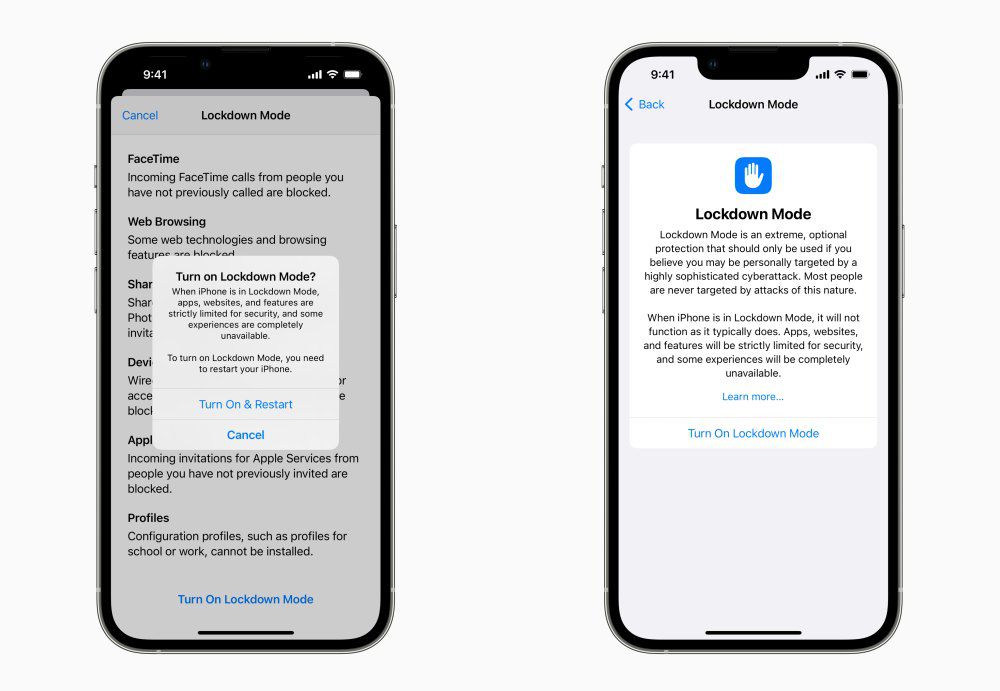
Apple calls it an “extreme, optional” level of protection that’s a clear response to the growing use of state-sponsored mercenary software like the Pegasus tool developed by NSO Group. Evidence of the software has been found on devices of journalists like Jamal Khashoggi. According to Bloomberg reporter Mark Gurman, Apple just released iOS 16 Developer Beta 3, which includes Lockdown Mode.
Related
NSO’s Pegasus spyware: here’s what we know
New analysis further links Pegasus spyware to Jamal Khashoggi murder
In past years, Apple had been criticized for not working with security researchers to find and close flaws in its platforms as much as other big tech companies before launching an iOS bug bounty program in 2016. It eventually expanded the program to cover other devices in 2019 while saying it would distribute special security research devices to outside researchers.
According to Apple’s head of security engineering and architecture, Ivan Krstić, “While the vast majority of users will never be the victims of highly targeted cyberattacks, we will work tirelessly to protect the small number of users who are. That includes continuing to design defenses specifically for these users, as well as supporting researchers and organizations around the world doing critically important work in exposing mercenary companies that create these digital attacks.”
While introducing the new operating systems at WWDC 2022 in June, Apple said its new Rapid Security Response feature will enable patches for security flaws that roll out faster and can take effect on a Mac without requiring a reboot. iOS 16 and macOS Ventura are also set to include support for new passkey technology that will help eliminate the use of passwords.
Related
Apple, Google, and Microsoft will soon implement passwordless sign-in on all major platforms
Other tech companies have made similar efforts in certain ways, like Google’s Advanced Protection Program for its accounts or the Super Duper Secure Mode Microsoft started testing in Edge last fall. Some small companies have also tried offering hardened devices running Android that promise protections against various vulnerabilities, but Lockdown Mode is a new level of security that will be available to millions of people once it launches with the new software updates later this year.
Even with these protections, finding vulnerabilities in the operating systems that control so many devices is a valuable endeavor, and Apple says it’s doubling the bounty for “qualifying findings” in Lockdown Mode to $2 million, which it says is the highest maximum bounty payout in the industry. Apple also says that any damages it’s awarded from a lawsuit filed last fall against NSO Group will be added to a $10 million grant to support organizations that “investigate, expose, and prevent highly targeted cyberattacks, including those created by private companies developing state-sponsored mercenary spyware.”