
Apple demoed technology at WWDC 2022 called Private Access Tokens — and they could potentially kill CAPTCHAs once and for all.
Private Access Tokens (PAT) can prove when an HTTP request is coming from a human instead of a bot. CAPTCHAs are the current form of authentication but it takes time for a human to complete one.
Known as the Completely Automated Public Turing test to tell Computers and Humans Apart, a CAPTCHA is an image or puzzle that appears on the web.
They start by clicking the "I'm not a robot" button. Distorted words, identifying objects in an image, or sliding a puzzle piece, these tools are an annoyance.
CAPTCHAs can also be compromised, such as being used to steal login information or come from a company that doesn't put privacy first.
PATs authenticate an HTTP request automatically in the background. Web users won't notice a thing, and cloud providers such as Cloudflare and Fastly are already incorporating the technology.
Authenticating people on the web
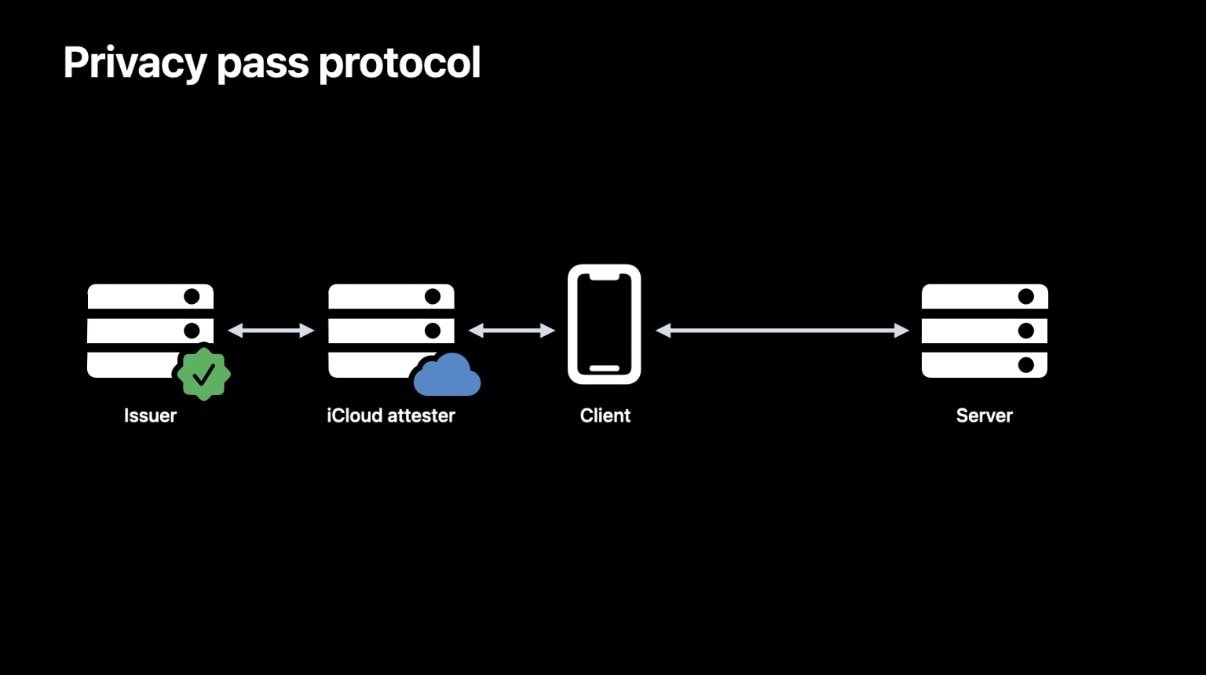
Using a new HTTP authentication method called PrivateToken, a server uses cryptography to verify a client passed an iCloud attestation check.
When the client needs a token it contacts an attester — in this case, Apple — which performs the process using certificates stored in the device's Secure Enclave. The attester can also perform something called rate-limiting.
Rate-limiting can recognize if the client device is following typical user patterns or is part of an iPhone click farm, as one example.
When an Apple user logs into their device with a password, Touch ID, or Face ID, open Safari and navigate to a website, their actions are hard for a bot to imitate.
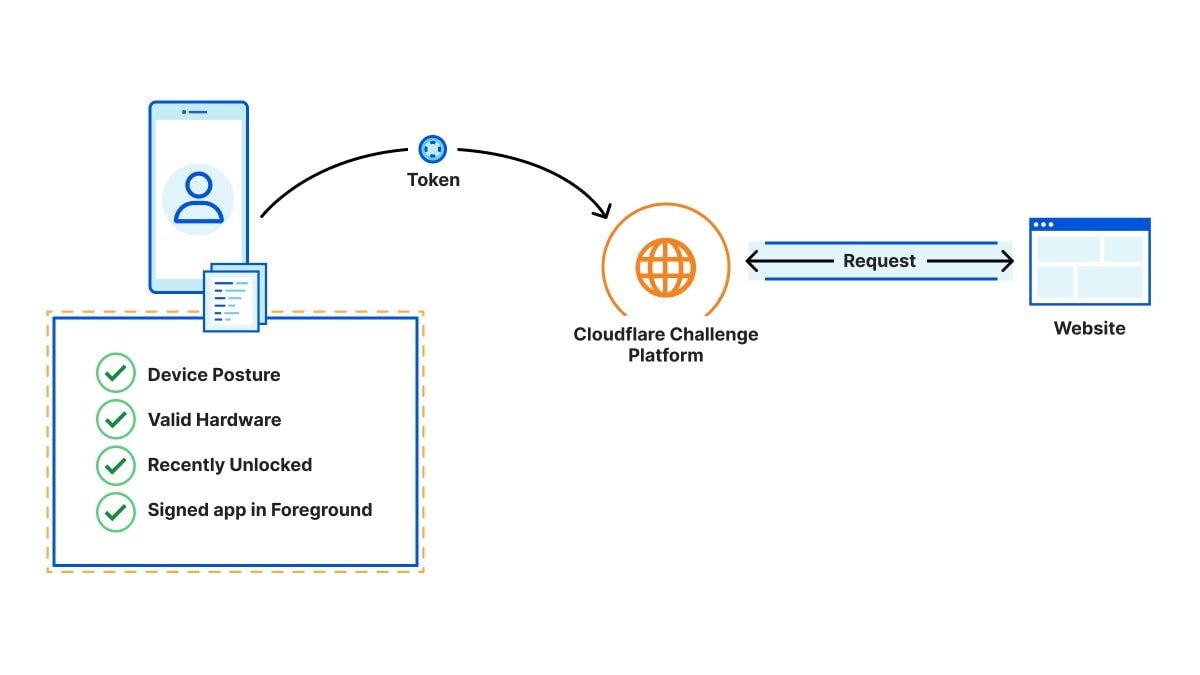
The signed token is eventually sent to the server in a multi-step process. The server doesn't know anything about the device or the person accessing it. But it trusts the attester and validates the token, and the person is taken to their destination web page.
Cloudflare explains that when PATs are used, device data is isolated and not shared between the parties involved in the process. Cloudflare knows the destination URL but not the device or user interaction information.
The website only knows the URL and client IP address, and the device manufacturer or attester only knows the minimum amount of device data required for attestation. It doesn't know the destination URL or the user's IP address.
Tokens are single-use as a way to limit replay attacks, which is when a client tries to present a token multiple times.
Web servers accessed through Safari and WebKit will work automatically with PATs. Other devices may not recognize the token process, so Apple cautions developers to make sure user authentication doesn't block the main web page and to present it as optional.
Apple says that these tokens require a device running iOS 16 or macOS Ventura or later with an Apple ID signed in. The Apple ID is only used for attestation and isn't shared.
It's an interesting move from Apple, and the goal of ending CAPTCHA is a noble one. It's also another way in which Apple users experience the web differently.
With technologies such as iCloud Private Relay, Hide My Mail, and App Tracking Transparency, Apple continues to limit exposure of personal information for its customers.
The company is working to help make Private Access Tokens a web standard, but there is no mention of tokens working on Android or Windows. People on those platforms may have to put up with CAPTCHAs, for now — or wait for Microsoft's and Google's work on the matter.