Keep your data safe with simple security practices

AppleInsider may earn an affiliate commission on purchases made through links on our site.
The Internet is a dangerous place, with many potential attacks that could be costly to your digital life. Here's how to keep your Mac, and your online identity, secure from threats.
In 2022, the number of attacks in cyberspace has increased significantly. According to Check Point Research, global attacks increased by 28% in the third quarter of 2022 compared to the same period in 2021.
Most of the threats that users face online are widespread and can be prevented by following basic rules of safe behavior on the Internet. It sounds easy, but according to a Fortinet 2022 Cybersecurity Skills Gap report, 80% of all breaches occur due to negligence of personal and corporate cybersecurity rules.
November 30th was celebrated as International Computer Security Day, and the MacPaw Cybersecurity team suggests that you figure out what threats exist and how to protect yourself and your Mac.
Who is at risk?
Anyone can suffer from attacks initiated by fraudsters in cyberspace. However, there are factors that make certain users more vulnerable. Among such factors:
Geolocation
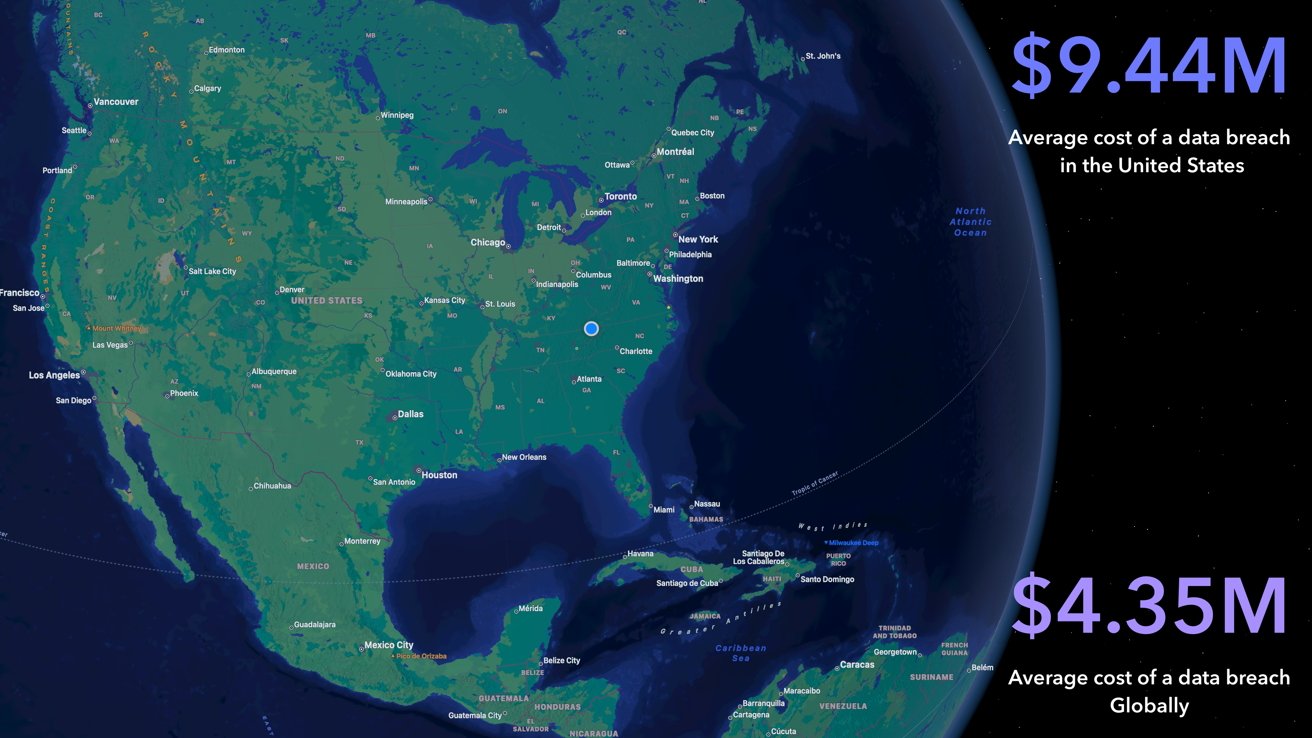
According to IBM's Cost of a data breach 2022 report, the USA is at the top of the list of countries and regions for the highest average cost of a data breach.
Workplace
Specialists who work in the government sector or critical infrastructure companies can become the target of hackers more often.
Position
Cybercriminals try to target those with the most access to sensitive information. Such people can be employees of the financial and legal departments of the company or system administrators.
A common fraudulent scheme is CEO fraud (or whaling attack) — attacks against the company's management. Often, C-level executives do not have time to attend corporate cybersecurity training, becoming the most vulnerable and, at the same time, the most desirable targets for criminals.
What to be protected from?
The standard list of risks in cyberspace has not been changing for more than ten years, but it is regularly supplemented with new and more complicated mechanics.
Incomplete security patching
The ethical hackers actually confirmed that Apple typically rolls out security patches for the current OS and the last two versions. So, if your Mac is operating on older macOS, it is time to improve it to ensure you're blocking the exploit.
How to protect yourself?
- Timely upgrade the OS and receive the latest security patches.
Malicious software
Loss of access to personal and corporate information, financial records, ransom demands, and costs for recovery of macOS and software are just some of the consequences of malware exposure. It usually affects the user's device due to carelessness when downloading suspicious files or working with unverified programs.
How to protect yourself?
- It is worth updating the macOS and versions of the programs you use. In order not to control this process yourself, enable automatic updates.
Formjacking
Formjacking is the theft of data from forms that a user fills out on websites. According to a report by Symantec, back in 2018, an average of 4,800 sites were hacked using this method every month.
Thus, by placing an online order on a previously hacked site and filling in bank details, the user gives access to money to the attacker.
How to protect yourself?
- Provide your personal data only to verified resources that you trust.
- Be careful with pop-up windows in your browser, applications, and OS.
- Always read push notifications and don't "accept" everything hastily.
Phishing
Phishing remains one of the most popular ways to steal user data. Cybercriminals improve their skills and learn from their mistakes. Scam emails may look normal, except they contain malicious links or fake landing pages, and may make the user share sensitive information (such as passwords or bank details).
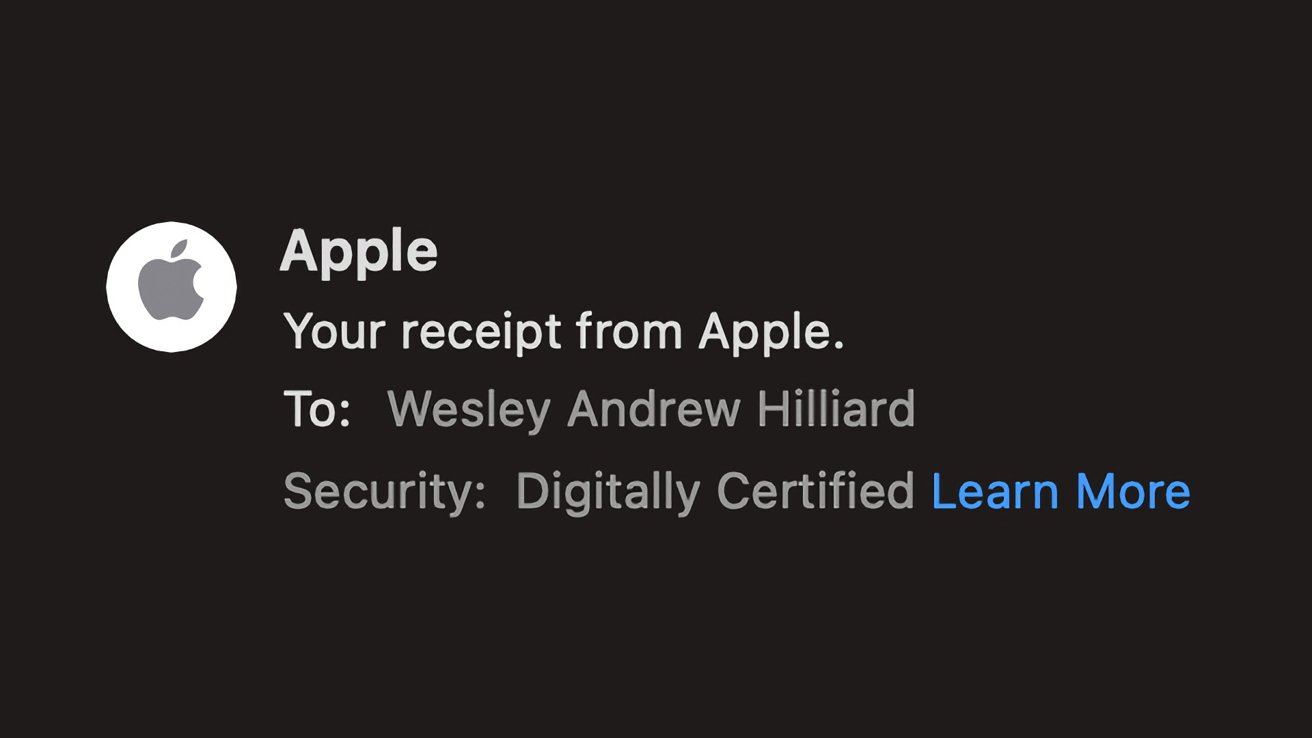
One of these options is sending fake reports to the company in the form of a letter from the accounting department.
How to protect yourself?
It's worth remembering one rule: if you don't expect it, it's suspicious.
- Pay attention to the details of incoming letters: the correctness of the sender's email address, the style of communication, the names of organizations, urgency, and prompting for immediate action. Always check website domain names before clicking on links. Attackers can change the domain name to look like legitimate resources (e.g., facelook.com, gooogle.com, etc.).
- Do not click, open or run suspicious files, links or programs unless you fully trust the source. Don't open suspicious URLs, especially those that lead to websites you don't normally visit.
- Send unwanted emails to the spam folder before opening. Files or links from people you don't know should be treated as malicious until you've verified otherwise. To do this, check the origin of the file through other communication channels. For example, if you received a file by email, contact the sender in the messenger and check whether they really sent the email.
- Try to be careful when using cloud services, especially when uploading sensitive information.
- Malicious URLs are sometimes "masked" as random text in HTML files, documents, and emails, or encoded as QR codes or "shortened" URLs. Do not open the link in your browser or scan QR codes by your smartphone if you are not sure of their origin. To check a link, hover over it without clicking, and the actual URL will appear. Or right-click the link and copy it into a text editor to see the address.
Typosquatting
The method is simple, which is why it is invisible to many users. Attackers change the URL of the site. For example, replace "com" with "org." A user who follows such a link gets to a malicious site that copies the interface of a website but aims to steal confidential information. 3% to 5% of attacked people responded to these mechanics.
How to protect yourself?
- Pay attention to the correctness of the site name, logo, and SSL security certificate. The icon in the form of a closed lock on the left in the address bar of the browser, in most cases, indicates that the connection is secure (uses an SSL security certificate).
- Prefer the HTTPS protocol because it is reliable and provides a secure connection and confidentiality of information through encryption.
- Trusted sites usually have a privacy policy section on the use of user data. Take the time and read the information.
Endpoint attacks
Hackers use this method to gain access to large networks. The target of such attacks are employees of companies who work outside the office space using cloud environments and remote workstations.
How to protect yourself?
- It's a good idea to follow your company's cyber security standards when working outside the office.
Attacks on supply chains
The criminal finds and exploits vulnerabilities in external services or software used by the target company. According to research by Zscaler, in 2021, the frequency of such attacks on technology companies increased by 2300%.
How to protect yourself?
- When using free applications and services, it is worth checking the activity of the development company, its motivation in creating and maintaining the program, analyzing the ways of monetization, and the latest update dates. After all, if it is not profitable for the developer to support the product, he will stop updating it, and the program will become vulnerable to cyber attacks.
IoT attacks
Here we are talking about smart home devices, cars, personal devices, household appliances, and medical devices through which access to your MacBook can be gained.

How to protect yourself?
- It is worth changing the default password on the devices to a reliable one and periodically updating it.
- Regularly update the software of IoT devices.
- Carefully analyze the traffic that goes to and from your devices.
- Set up two-factor authentication.
- Use only a reliable Wi-Fi encryption algorithm.
What tools to use to defend?
There is a longstanding myth that Macs are immune to viruses. According to the research, Windows and Mac users were similarly affected by viruses (10.3 percent of Windows clients compared to 8.3 percent of Apple customers). Here are a few tools which can be used to defend your Mac.
Antiviruses
Bitdefender
Bitdefender is an antivirus that offers protection against viruses without requiring a large subscription fee. The user will receive Safepay online banking protection, a password manager, a vulnerability scanner, and other features.
Norton AntiVirus
Norton AntiVirus is an antivirus software with additional features that are not always found in other programs. Specifically, a built-in cloud backup tool that provides 2GB of online storage.
Pareto Security
Pareto Security's paid auditor and updater checks whether your Mac is properly configured, with an up-to-date version of the operating system, and whether there are any security threats to the device. This allows you to prevent 80% of risks.
Useful services
SpyBuster
58% of all cyber attacks in the world come from Russia, therefore, a general recommendation when choosing protection programs is to avoid services of Russian production. Unfortunately, 29% of Russian cyberattacks are successful, and in a quarter of cases, hackers get the data of the organizations or users they are hunting.
SpyBuster, crafted by MacPaw, will help you protect yourself from malicious Russian software. The free program helps protect your Mac against potential spying apps and connections on the device.
SpyBuster scans the device for installed programs with connections to Russia and monitors whether users' personal data is sent to Russian servers.
This is especially important, considering that in 2016, Russia adopted the Yarova Law, which obliges companies to store private user data (message content, sender and recipient information, location, etc.) on Russian servers. The law allows the FSB and similar Russian entities unlimited access to this data without a court order.
1Password
1Password is a password manager that lets you create, store and share passwords in a secure environment, even with those who aren't subscribed to it. A free alternative can be KeePassXC, but it only works locally on one device.
ClearVPN
MacPaw's ClearVPN service helps to keep your online presence secure and is governed by international data encryption protocols. Regardless of the purpose of the Internet: viewing news, correspondence in messengers, or watching movies, ClearVPN provides reliable Internet protection and data anonymity.
VirusTotal
VirusTotal is a free service by Google that checks suspicious files for all types of malware with more than 50 antiviruses at the same time. However, the free version has a file size limit of 650 MB.
Hybrid Analysis
Hybrid Analysis is a sandbox that allows you to scan your file for viruses and malware for free. The service allows you to download and run a suspicious file in a secure environment to test it for malicious behavior.
Talos Intelligence and Reputation Center
Talos Reputation Center detects threats in real-time using the world's largest threat detection network. It includes web queries, emails, malware samples, open-source datasets, endpoint analysis, and network intrusions.
Thanks to their tools, you can check files, emails, and IP addresses for involvement in suspicious activity.
Also, here are several services to check the content for malware.
- have i been pwned lets you check if an account has ever been hacked.
- PhishCheck lets you check if a link is phishing.
- Simple Email Reputation checks whether the sender of the email has previously been seen in phishing or spam emails.
- WhereGoes checks where the link actually goes. Useful for shortened URLs.
- Objective-See creates free, open-source applications to protect macOS. Knock-knock lets you check what software is permanently installed on your Mac. Malware is constantly installed on the computer to automatically run every time the device is rebooted. KnockKnock detects such programs to enable the user to check them and remove malicious ones.
- macOS Security Compliance Project - an open-source solution for users who want to independently test their Mac for compliance with a specific security standard (such as DISA or STIG).
Author Oleksii Myronenko is a Product Manager at CleanMyMac X by MacPaw, where he builds features that keep Macs clean and healthy. He is a strong believer that both machines and humans need to be in good shape, Oleksii loves playing football and sharing advice on Mac care.